Which of the Following Best Describes Encryption
336 Sound Fiscal and Business Practices. If it is not selected the encryption type will not be allowed.

Solved Which Of The Following Best Describes What Is Meant Chegg Com
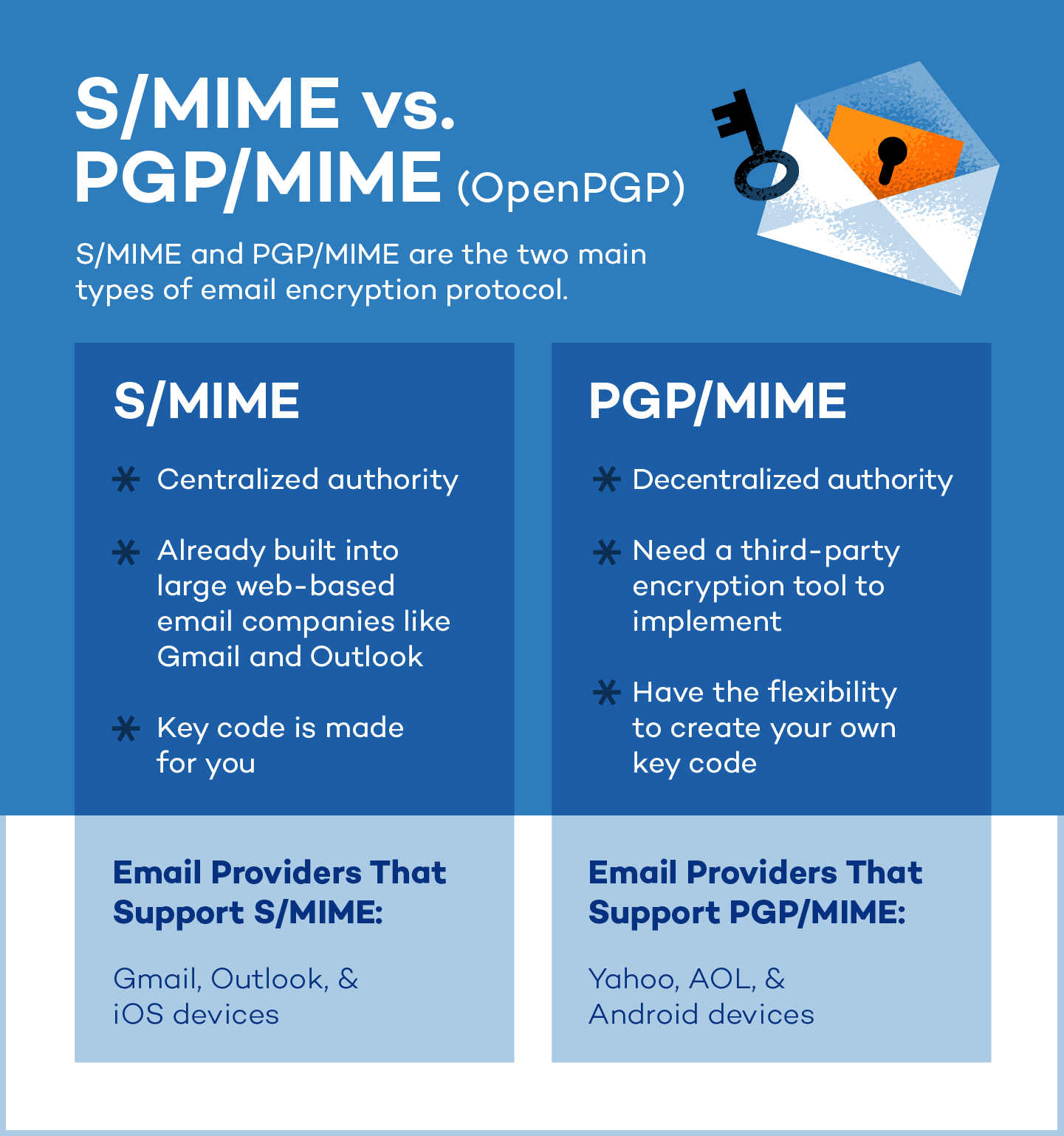
Example of ECB mode.
. Encryption can be used for good or bad and even the definition of whats good or bad encryption varies depending on who you ask. People use them to store an incredible amount of personal information from our private conversations to our photos our music our notes our calendars and contacts our financial information and health data even where we have been and where we are going. Encrypting the exchanged data to keep it secure from eavesdroppersThat means that while the user is browsing a website nobody can listen to their conversations track their activities across multiple pages or steal their.
Best available This refers to a group of writers who are good at academic writing have great writing skills but are new in our team of writers. Airflow needs to know how to connect to your environment. Financial firms have sensitive data including credit card numbers social security numbers financial history etc.
Contractors must demonstrate business procedures and internal controls that prevent the following practices. Based on the sensitivity of the data it needs to be secured and protected from unauthorized. This configuration applies to MR Access Points only.
At the time of this documents publication Google uses the following encryption algorithms for encryption at rest for DEKs and KEKs. This group of writers have passed strict English tests plus tests from their fields of specialization. Deploying AWS CDK apps into an AWS environment a combination of an AWS account and region may require that you provision resources the AWS CDK needs to perform the deployment.
The CryptoLocker ransomware attack was a cyberattack using the CryptoLocker ransomware that occurred from 5 September 2013 to late May 2014. The Need for Encryption. This section describes the prerequisites for using BitLocker Drive Encryption on the Windows endpoints in your network the various authentication modes available and how they interact with the proprietary group policy settings.
SQL Server Column Level Encryption Example using Symmetric Keys. The process of provisioning these initial. This means they recently joined the team.
If the contractor fails to use the FIPS 140-2 level of encryption the contractor must report a breach of confidentiality to the assigned regional program specialist and TWC contract manager. Enter the following command to configure FortiOS to use only strong encryption and allow only strong ciphers AES 3DES and digest SHA1 for HTTPS SSH TLS and SSL functions. Nitansh Agarwal Updated.
The attack utilized a trojan that targeted computers running Microsoft Windows and was believed to have first been posted to the Internet on 5 September 2013. Information such as hostname port login and passwords to other systems and services is handled in the Admin-Connections section of the UI. This section describes some best practices for employing stronger and more secure encryption.
Smartphones led by iPhone have become an essential part of our lives. One of the best options for securing files on your computer and on external drives is a free open source disk encryption utility called TrueCrypt. The Tink encryption library supports a wide variety of encryption key types and modes and these are reviewed regularly to ensure they are current with the latest attacks.
Perhaps classifying encryption as munitions makes the most sense if you support 2A rights. Is Always Encrypted SQL Server 2016s most widely important new feature. McAfee Safe Connect uses an AES 256-bit encryption which is considered one of the most secure encryption methods and is the standard adopted by large agencies such as banking and government institutions.
It is significant that Always Encrypted in SQL Server is in all editions of SQL Server. The pipeline code you will author will reference the conn_id of the Connection objects. These resources include an Amazon S3 bucket for storing files and IAM roles that grant permissions needed to perform deployments.
2011-11-22 Comments 52 Related. This includes all information storage objects containers and types that exist statically on physical media whether magnetic or optical disk. Because of the increasing importance of encryption to data governance it allows encryption for the sensitive application data for everywhere beyond the applications client connection including network.
The plain text is the ASCII encoding of Now is the time forThat is the 19-byte sequence 4E 6F 77 20 69 73 20 74 68 65 20 74 69 6D 65 20 66 6F 72We are encrypting using DES in ECB mode with the cryptographic key 0x0123456789ABCDEFTo encrypt we break up the plaintext into blocks of 8 bytes Note we are using 8 in this example. Best practices for Azure data security and encryption relate to the following data states. It works with Windows Linux and Mac and allows you to encrypt an entire drive partition or flash drive or create an encrypted file store in which you can store sensitive data files and take them with you.
Data sent using HTTPS is secured via Transport Layer Security protocol which provides three key layers of protection. Unfortunately I see it increasingly being used to oppress users in the form of DRM and other security features. It propagated via infected email attachments and via an existing.
This difficult-to-hack encryption ensures that all sensitive data traveling through McAfee Safe Connect VPN remains secure and private. This article describes how to configure name and enable each SSID so that each provides the proper level of access to connected clients. Turn on global strong encryption.
This policy setting allows you to set the encryption types that the Kerberos protocol is allowed to use. This security policy reference topic for the IT professional describes the best practices location values and security considerations for this policy setting. Consult the following whitepaper to learn more about Wireless Guest Access at the Office.

Inf 103 Week 4 Quiz Social Networking Sites Powerpoint Presentation Online Learning
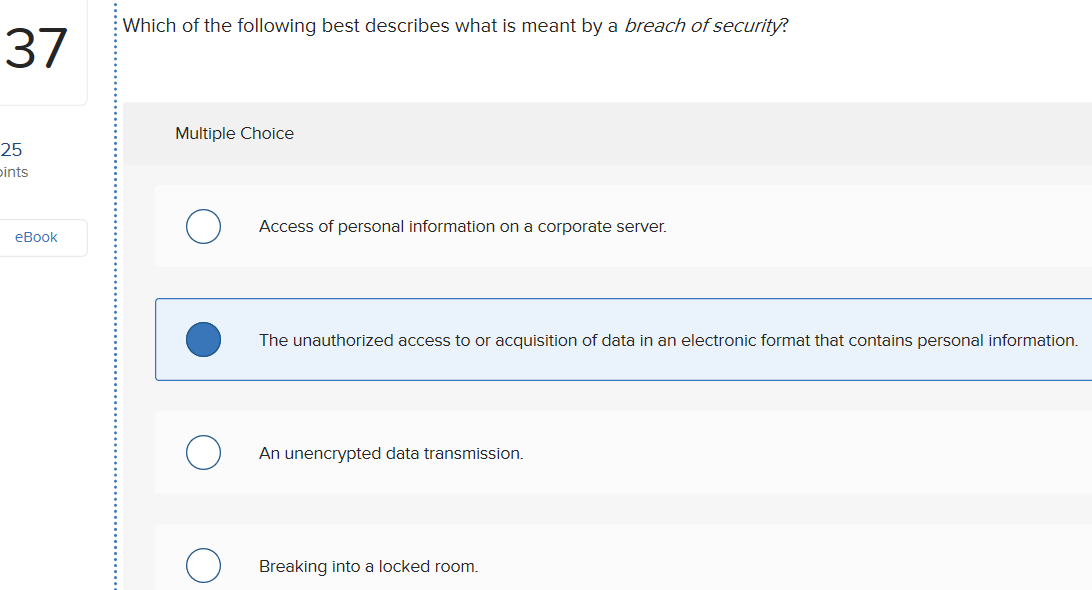
Solved Which Of The Following Best Describes What Is Meant Chegg Com
0 Response to "Which of the Following Best Describes Encryption"
Post a Comment